
Financial institutions such as banks, trading firms, and insurance companies engage with individuals, businesses, and governments for their financial needs and management. Cloud adoption in the financial industry is slower than many others due to regulatory scrutiny, risk aversion, or entrenched legacy technology.
As cloud computing becomes the dominant computing paradigm within a financial institution, it will lead to structural changes that impact processes, personnel, and technology.
Consider the following to deploy the financial institutions’ application in the cloud as a service:
Security, Risk, and Compliance
Financial institutions are well aware of security risks and top cybercrime targets. They thoroughly evaluate the cloud solution security capabilities like SOC 1/2/3 attestation, governance about how data moves within the cloud and in the multi-cloud environment, data integrity and confidentiality controls, and operational and technical implications for protecting data.
Ecosystem Management
Financial institutions work with a large ecosystem of vendors for software, IT services, or other services for their on-prem environments. Moving to the public cloud brings challenges like working with new partners or third-party vendors and maintaining data integrity and operations during the cloud migration. It also brings new revenue streams and opportunities for financial institutions to offer new digital services and to work with new customers and organizations.
Mergers and Acquisitions
Financial institutions acquire other financial institutes to expand their footprints, solve unique use cases, and increase revenues. These entities built their network independently and can create problems when merging both companies’ networks.
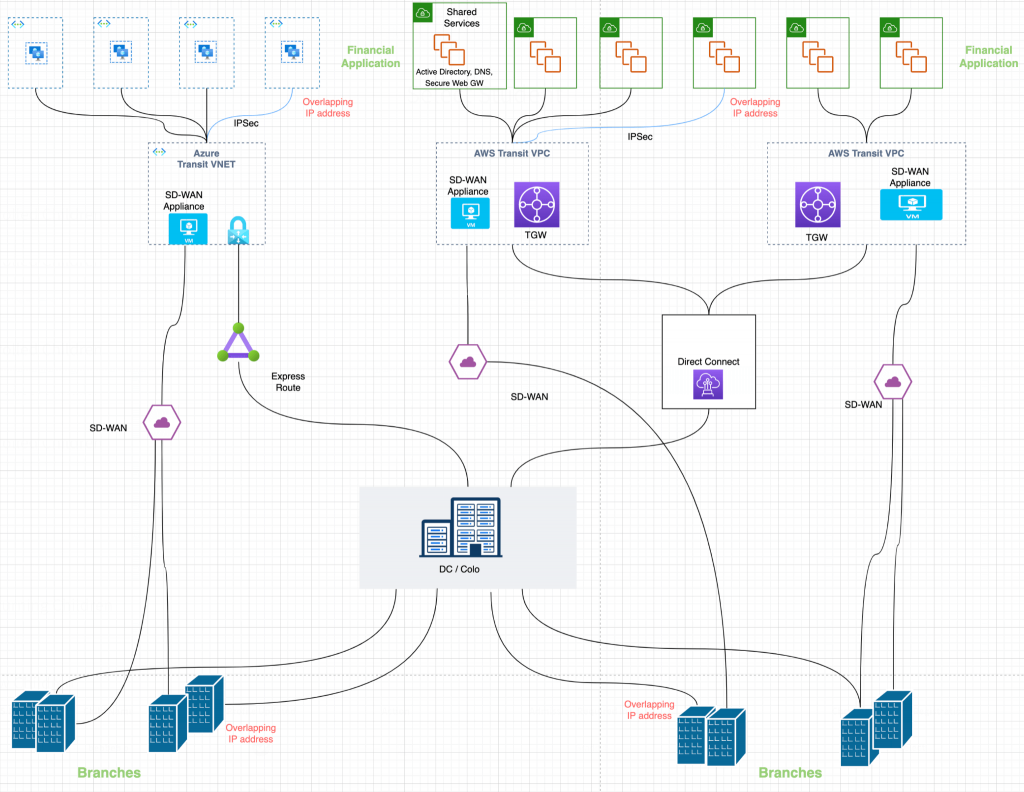
Figure 1: Financial Institutions Cloud Architecture Example
Technical Requirements
Strong Encryption
Financial institutions deal with many applications and services between clients and institutions and between institutions that can not be exposed to the Internet without strong IPSec encryption. These applications and services include financial transactions, secure access to banking apps, etc.
Resiliency
Outages are always a major concern, especially for mission-critical workloads. The two main risk areas are infrastructure availability and service availability for applications built on the infrastructure. That said, availability is critical for financial institutions, which drives toward the hybrid and multi-cloud models despite the challenges that no CSP architecture is perfect for all purposes and has different constructs and limitations.
Latency
The geographic distance between the data centers of a financial institution and a CSP affects latency and performance. Mission-critical and core banking workloads require strict SLAs such as credit card authorization round-trip time, which often require ultra-low latency. Latency becomes a key challenge for the financial institution to migrate to the public cloud because each CSP latency differs for different use cases.
Compliance Requirements
The location of data raises multiple issues of ownership and geography. Regulatory requirements impose further constraints. Many institutions face voluntary or externally mandated limits on storing data types.
CSPs have been easing the concerns of regulators and financial institutions through third-party security certifications and attestations (such as SOC or ISO).
Integration with SD-WAN vendors
Financial institutions use SD-WAN solutions for their Onprem Branch to Branch and Branch to Data center connectivity. As they are migrating their workloads to the public clouds, they want to do the investment protection and ensure CSPs offer seamless integration with various SD-WAN vendors.
Network Address Translation (NAT)
Typically, merging financial entities are designed independently, resulting in a high probability of overlapping IP ranges. Often, financial institutes don’t have access to the client’s network, forcing them to look into the NAT capabilities of the solution to solve this challenge.
Shared Services
Financial Institutions IT services such as Microsoft AD, CDN, DNS, NTP, or DHCP services are hosted in a shared VPC/VNET and need to be accessed from on-prem and third-party vendors.
Alkira Cloud Area Networking for Financial Institutions
Alkira Cloud Area Networking is the first global unified multi-cloud network delivered as-a-service. Alkira seamlessly solves all the financial institutions’ network requirements and challenges mentioned above. Alkira allows financial customers to quickly onboard their infrastructure leveraging various methods, including AWS Direct Connect, Azure Express Routes, SD-WAN, and IPSec Connections from third-party clients into the Alkira Cloud Exchange Points. At the same time, customers also connect their cloud workloads (VPCs, VNETs) to the Alkira Cloud Exchange Points achieving seamless high-bandwidth multi-cloud connectivity for financial applications. Alkira’s solution also allows customers who want to inspect or steer the traffic between on-premises to cloud or multi-cloud environments to use the policy drive framework to inspect or steer traffic as per the requirements.
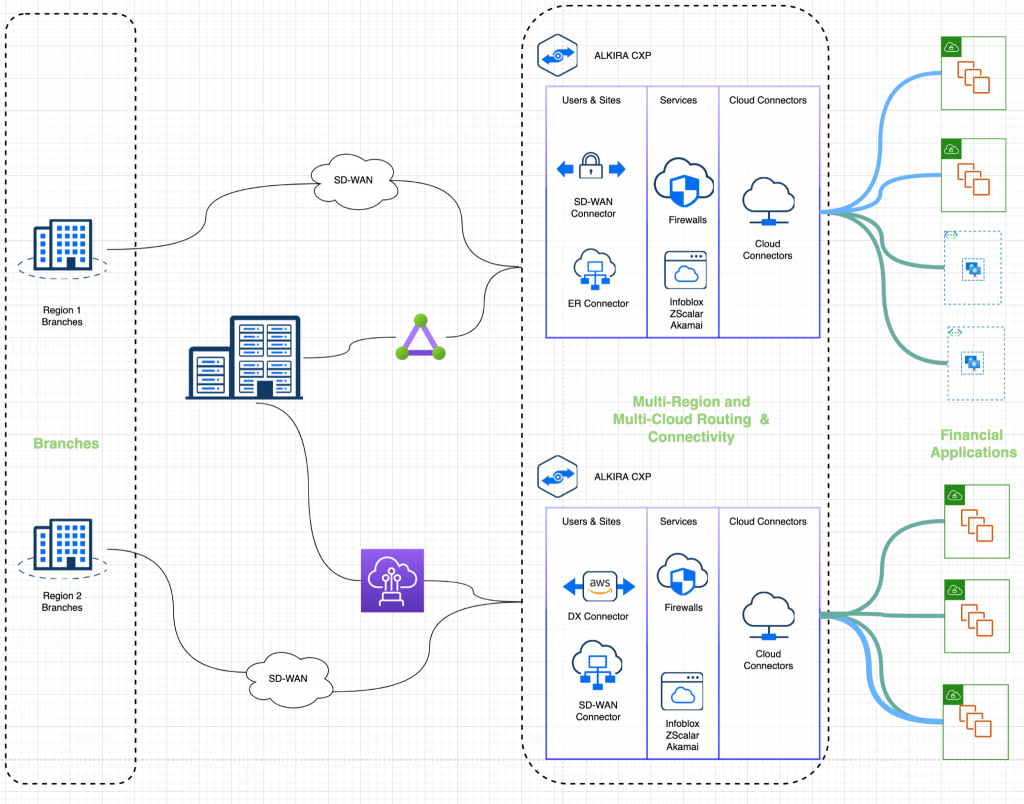
Figure 2: Alkira Cloud Area Networking for Financial Applications
The above architecture diagram shows a high-level topology for a typical financial company leveraging Alkira Cloud Area Networking. On the on-premises side branches, data center/colocation, third-party clients would build connectivity into the Alkira CXP using private connections like Direct Connect or Express Route or IPsec connections or SD-WAN connections. On the cloud side, the connections will be from the VPCs/VNETs where the financial application exists. Also, shared services VPC/VNET exist on the cloud side; these VPC/VNETs will build connectivity to the CXP. Once this is completed, end-to-end connectivity is established between the on-premises and cloud environments. Customers can also choose to inspect traffic using the firewall as per their requirements using Alkira’s policy-driven framework.
Alkira Solution Benefits
Latency
Customers can connect to the Alkira CXP in the nearest region depending on where the applications exist and then leverage Alkira Backbone to have low latency while connecting to these applications. This can help with applications that are latency sensitive and help with efficient connectivity.
Segmentation
Alkira can provide isolation of workloads and communication from third-party clients. Traffic across segments can be inspected as well. Since a segment represents a unique routing and policy space, maintaining isolation becomes seamless for customers.
Refer to this blog for more details about cloud network segmentation.
High availability and Redundancy
Alkira infrastructure is highly resilient and redundant and can spread across multiple regions, and availability across multiple clouds like AWS, Azure, GCP, OCI, etc. This will allow the providers to meet their critical SLA requirements.
Seamless Firewall Integration
Alkira provides seamless integration with vendors like Fortinet, Check Point, and Palo Alto for traffic inspection for any type of traffic flow. Financial companies get a significant advantage as they don’t have to bring up firewalls depending on traffic flow. Also, functionality like autoscaling comes as part of the solution, which helps to scale up or down depending on the requirements.
For more details, please refer to this blog about multi-cloud inline traffic inspection.
Advanced Overlapping IPs Solution
The Alkira CXPs or cloud exchange points form a networking fabric in the cloud that you can connect to on-premise sites like SD-WAN or standard IPsec sites and connect your cloud networks using native constructs. Once these on-prem sites and cloud networks like VPC or VNets are connected to the Alkira CXPs – where overlapping IP spaces are allowed, Alkira’s policies can be applied network-wide to them, and part of the policy is NAT.
For more details, please refer to this blog about solving overlapping IPs in a multi-cloud environment.
Resource Sharing
Using the Alkira solution, customers can use the Resource Sharing feature to handle the shared services use case. Resource sharing allows them to choose specific resources by identifying the network prefixes to be shared across two segments and enabling additional capability to allow an inline firewall to inspect the traffic for Resource sharing.
For more details, please check out our blog on resource sharing.
Automation with Terraform
Network Infrastructure deployment at a large scale requires automation, and Alkira helps to solve this wherein the customer can use terraform to provision the network infrastructure for Alkira.
Conclusion
Alkira Cloud Area Networking infrastructure provides financial companies with an easy and secure solution with all the regulatory compliance requirements.
Reach out and schedule a demo today to learn more about how Alkira can help simplify cloud area networking for your organization. You can also try our Cloud Insights tool for free, giving instant inventory and insights into your cloud networking resources.
Ahmed Abeer is a Sr. Product Manager at Alkira, where he is responsible for building a best-in-class Multi-Cloud Networking and Security Product. He has been in Product Management for more than ten years in different big and small organizations. He has worked with large enterprise and service provider customers to enable LTE/5G MPLS network infrastructure, automate Layer 3 Data Center, enable Next-Gen Multi-Cloud architecture, and define customers’ Multi-Cloud strategies. Ahmed’s technical expertise in Cloud Computing and Layer 2/Layer 3 network technologies. Ahmed is a public speaker at various conferences & forums and holds a Master’s Degree in Computer Engineering
Deepesh Kumar is a Solutions Architect and product specialist in the computer networking industry with over 8 years of experience. He currently works as part of the post sales team at Alkira and focuses on working with customers to design and deploy the Alkira solution. Prior to working here, he worked at Viptela which was acquired by Cisco Systems. He holds a masters degree from San Jose State University.





