
Network security is paramount in its importance. In a world where applications are distributed across hybrid-cloud and multi-cloud environments, and user access is ubiquitous, traditional security architectures based on castle-and-moat model fall short in providing adequate protection against the ever-expanding landscape of security threats. Public clouds provide the convenience of global availability, high scale, and easy consumption, allowing rapid applications and services deployments coupled with DevOps agility, but they often overlook the enterprise needs for robust networking and network security architecture.
To that end, Alkira Cloud Area Networking offers a global, scalable, and secure virtual cloud infrastructure where enterprises can design, deploy, and operate hybrid-cloud and multi-cloud networks in minutes. Alkira’s network services marketplace offers a choice of Alkira and 3rd party network and security services, with full life-cycle management and integration into the network fabric. All are offered as-a-service.
We are proud to be a member of the Cisco Secure Technical Alliance partner ecosystem and provide our joint customers a consistent experience for securing their hybrid-cloud and multi-cloud networking environments leveraging Cisco Secure Firewall Threat Defense. The firewalls are deployed within the globally distributed Alkira Cloud Exchange Points (Alkira CXPs) offering unmatched security controls, such as stateful firewalling, Snort3 IPS, URL filtering, malware defense, application visibility and control, and more for the application traffic traversing the Alkira Cloud Backbone.
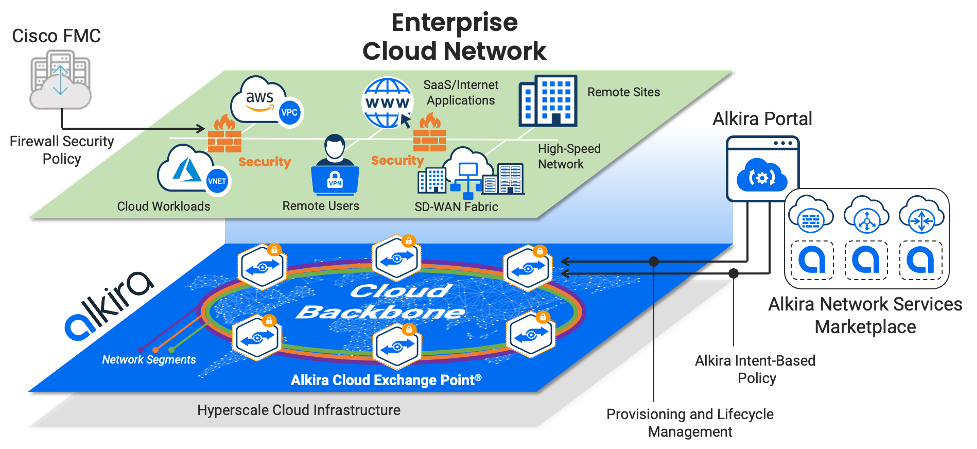
Figure: Alkira Cloud Area Networking platform with integrated Cisco Secure Firewall Threat Defense.
IT security teams continue leveraging Cisco Secure Firewall Management Center (FMC) for consistent security policies across the Cisco firewalls deployed within the Alkira virtual infrastructure, as well as the Cisco firewalls deployed in the traditional non-Alkira environment. This approach ensures compatibility with brownfield environments and maintains a consistent security policy during the time of migration into the Alkira Cloud Area Networking platform.
Alkira policy infrastructure allows defining intent-based policies to steer all or selective application traffic to the Cisco firewalls where security policy is enforced. Alkira’s solution makes sure to maintain flow symmetry for traffic traversing numerous firewalls within a single Alkira CXP and across multiple Alkira CXPs. In the latter case, the intelligent traffic steering prevents duplicated firewall inspection and effectively doubles the overall firewalling capacity.
But what if additional firewall capacity is needed? As application traffic patterns change, Cisco firewalls deployed with the Alkira CXPs may receive increased (or decreased) amounts of traffic. Alkira’s solution auto-scales up and down the Cisco firewall footprint to accommodate the real-time capacity demand. When additional firewall capacity is needed new Cisco firewall instances are automatically instantiated, licenses get applied, security policy gets propagated, and traffic flows are symmetrically distributed across the larger firewall pool. All that without any administrative intervention. How cool is that!
Enterprises are choosing the joint solution of integrating Cisco Secure Firewall Threat Defense with the Alkira cloud network as-a-service platform to address the following main use cases:
- Hybrid-Cloud and Multi-Cloud Security: Cisco firewalls provide a centralized security policy enforcement for application traffic to (north-south) and inside (east-west) the cloud environments attached to the Alkira platform.
- Branch and Data Center Security: Cisco firewalls secure the communication between enterprise on-premises sites attached to the Alkira platform. This east-west communication passes through the Alkira Cloud Exchange Points, but it is not destined for any public cloud environment.
- Secure Internet Edge: Outbound/egress Internet traffic originated from either on-premises sites or cloud environments attached to the Alkira platform is subjected to the Cisco firewall security policy.
- Cloud DMZ: Inbound/ingress traffic from external sources destined to the Internet-facing applications deployed in on-premises data centers or public cloud environments attached to the Alkira platform is subjected to the Cisco firewall security policy.
- Shared Application Services: Cisco firewall security policy is enforced on cross-segment application traffic in support of business partner integration, mergers, acquisitions, and divestitures scenarios.
In a world dominated by clouds, do not let your security fall behind. Get on-board the Alkira cloud area network platform with integrated Cisco Secure Firewall Threat Defense and see how you can transition your network and network security into the cloud era in minutes.
Request your personalized demo here.
Read a Cisco-Alkira joint solution brief here.
Read Cisco blog here.



Leave A Comment